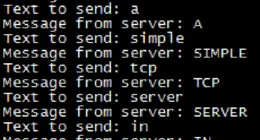
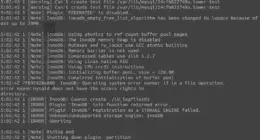
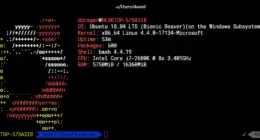
I put this together for a project in a class I am…
Browsing Tag
password
3 posts
Social Media and the Downfall of the Password Reset Question
There have been a number of high profile account compromises due to…
Password Protected Folder Gives 404 Not Found in WordPress Installation Sub-folder.
Came across this little maddening issue again today after fixing it a…