I put this together for a project in a class I am taking, and thought it would be handy for others as well. The goal is to access a Windows filesystem and reset the password for a user, for example if someone forgot the Administrator password or the account is locked out from too many bad password login attempts. This works on all modern Windows Operating Systems: Windows 2000, 2003, XP, Vista, Win7 etc. Make sure to create a backup if you want to make sure you don’t corrupt your Windows install, as it can happen.
Tools used:
- Unetbootin
- Ubuntu 9.10 Desktop ISO
- One flash drive, 1 gig or larger
- chntpw
Accessing the Filesystem
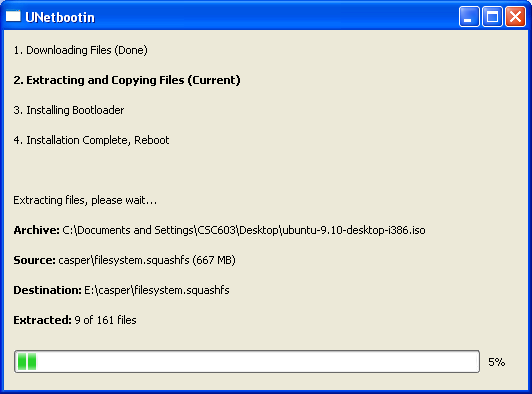
First we use unetbootin to install Ubuntu 9.10 to a flash drive. The flash drive needs to be at least 1GB to install the image.
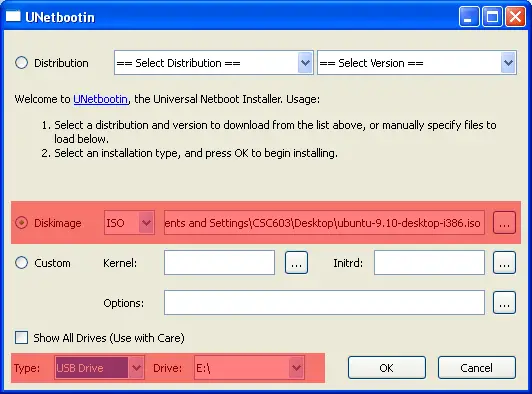
Select “Diskimage” and then the .iso file we downloaded of the Ubuntu 9.10 image.
Select the USB Drive and Drive Letter to install the ISO onto. Click OK:
Once the program is done, click ‘exit’ and remove the USB Drive. You now have a bootable live image of Ubuntu 9.10.
Plug the usb drive into the target system. Boot off of the drive, you may need to change the boot options in the BIOS if it is set to boot off of the hard drive. Select “Default” in the unetbootin boot menu to boot into the Ubuntu OS. It will automatically log you in.
Once booted you already have access to the Windows filesystem since the ntfs filesystem driver is included in the kernel. This is nice and wasn’t the case not too long ago.
We chose two reasons to use unetbootin and Ubuntu 9.10. The first is the ease of use of installing a bootable image. After downloading the two packages, it is trivial to load the OS onto the drive, and since it includes ntfs drivers it allows us to access the unencrypted hard drive on boot. Since it is on a USB drive, any system made since 2000 or so should be able to boot this. You don’t need to lug around a CD or even access the CD drive.
To prevent easy access to the hard drive, encryption of the hard drive partition would be necessary using Microsoft EFS or TrueCrypt hard drive encryption software. After encrypting the hard drive, any live operating system running would not be able to decrypt the hard drive easily.
Furthermore, installation of a BIOS level password would ensure that any unauthorized users would not be able to boot alternative operating systems via USB, CDROM, Floppy or other method. The only way to defeat a BIOS level password would be to reset the BIOS (requiring entrance into the hardware of the system) or using an Evil Maid style attack.
The Evil Maid attack is performed by a theoretical malicious party that has access to the target PC without alerting the legitimate user. Without knowledge of the authorized; a root kit or device would be installed (for example, on the USB connector of the keyboard) to sniff out the password as entered on bootup. After the user boots the system and finishes her work, ostensibly shutting down the system securely, at least to her knowledge, the Evil Maid would then collect the password entered into the BIOS, thereby defeating the BIOS password security measure.
Resetting the Password
We can now reset the Administrator or any other password on this system using the tool chntpw. To install this package, ensure the system has a connection to the internet (via dhcp perhaps?) and run the command:
sudo software-properties-gtk --enable-component=universe --enable-component=multiverse; sudo apt-get update; sudo apt-get install chntpw
Alternatively, you can download the executable and place it on the USB drive to give access without connecting to the internet. chntpw is the software that modifies the SAM (Security Accounts Manager) database file. Use the terminal to change directories to the password file
cd /media/path/to/disk/WINDOWS/system32/config/
Then execute the chntpw utility:
# sudo chntpw -u username SAM SYSTEM
View the sample output:
ubuntu@ubuntu:/media/B830C9BC30C981BC/WINDOWS/system32/config$ sudo chntpw SAM SECURITY chntpw version 0.99.5 070923 (decade), (c) Petter N Hagen Hive <SAM> name (from header): <\SystemRoot\System32\Config\SAM> ROOT KEY at offset: 0x001020 * Subkey indexing type is: 666c <lf> Page at 0x7000 is not 'hbin', assuming file contains garbage at end File size 262144 [40000] bytes, containing 6 pages (+ 1 headerpage) Used for data: 255/20736 blocks/bytes, unused: 9/3648 blocks/bytes. Hive <SECURITY> name (from header): <emRoot\System32\Config\SECURITY> ROOT KEY at offset: 0x001020 * Subkey indexing type is: 666c <lf> Page at 0xe000 is not 'hbin', assuming file contains garbage at end File size 262144 [40000] bytes, containing 13 pages (+ 1 headerpage) Used for data: 1074/49024 blocks/bytes, unused: 9/3808 blocks/bytes. * SAM policy limits: Failed logins before lockout is: 0 Minimum password length : 0 Password history count : 0 | RID -|---------- Username ------------| Admin? |- Lock? --| | 01f4 | Administrator | ADMIN | dis/lock | | 03ec | ASPNET | | dis/lock | | 03ed | CSC603 | ADMIN | dis/lock | | 01f5 | Guest | | dis/lock | | 03e8 | HelpAssistant | | dis/lock | ---------------------> SYSKEY CHECK <----------------------- SYSTEM SecureBoot : -1 -> Not Set (not installed, good!) SAM Account\F : 1 -> key-in-registry SECURITY PolSecretEncryptionKey: 1 -> key-in-registry ***************** SYSKEY IS ENABLED! ************** This installation very likely has the syskey passwordhash-obfuscator installed It's currently in mode = -1, Unknown-mode SYSKEY is on! However, DO NOT DISABLE IT UNLESS YOU HAVE TO! This program can change passwords even if syskey is on, however if you have lost the key-floppy or passphrase you can turn it off, but please read the docs first!!! ** IF YOU DON'T KNOW WHAT SYSKEY IS YOU DO NOT NEED TO SWITCH IT OFF!** NOTE: On WINDOWS 2000 it will not be possible to turn it on again! (and other problems may also show..) NOTE: Disabling syskey will invalidate ALL passwords, requiring them to be reset. You should at least reset the administrator password using this program, then the rest ought to be done from NT. Do you really wish to disable SYSKEY? (y/n) [n] RID : 0500 [01f4] Username: Administrator fullname: comment : Built-in account for administering the computer/domain homedir : User is member of 1 groups: 00000220 = Administrators (which has 2 members) Account bits: 0x0210 = [ ] Disabled | [ ] Homedir req. | [ ] Passwd not req. | [ ] Temp. duplicate | [X] Normal account | [ ] NMS account | [ ] Domain trust ac | [ ] Wks trust act. | [ ] Srv trust act | [X] Pwd don't expir | [ ] Auto lockout | [ ] (unknown 0x08) | [ ] (unknown 0x10) | [ ] (unknown 0x20) | [ ] (unknown 0x40) | Failed login count: 1, while max tries is: 0 Total login count: 1 - - - - User Edit Menu: 1 - Clear (blank) user password 2 - Edit (set new) user password (careful with this on XP or Vista) 3 - Promote user (make user an administrator) 4 - Unlock and enable user account [probably locked now] q - Quit editing user, back to user select Select: [q] >
Depending on the status of the SYSKEY password security, you may only be able to blank the password and not actually change it. I recommend blanking the password and then resetting it once you log into the system.
You can also unlock a system if the user accounts have all been locked out due to too many login attempts or any other reason. Using these tools you can gain access to almost any unencrypted Windows system, from Windows NT up to Windows 7.
As a warning, If there is data on the hard drive you wish to keep, make sure to make a backup of the hard drive before performing this password as it can corrupt the Windows installation.

5 comments
excelent….dude…
thanx.yar…..
excelent….dude…
thanx.yar…..
Works with Win7 :) Thanks a lot.
Awesome… glad to hear!
Comments are closed.