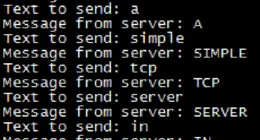
While doing any sort of development for an Internet of Things (IoT)…
Browsing Tag
http
6 posts
Firesheep Should Be A Call To Arms For System, Network & Web Admins
Firesheep by Eric Butler has just been released to the world. This Firefox plugin does a few things that have already been fairly easy to do for a while, but rolled up in one easy to use package:
Sniffs data on unencrypted Wireless Networks
Looks for unencrypted login cookies sent to known popular insecure sites
Allows you to login to that account with ‘One Click’
So what sites are impacted by default? Amazon.com, Basecamp, bit.ly, Cisco, CNET, Dropbox, Enom, Evernote, Facebook, Flickr, Github, Google, HackerNews, Harvest, Windows Live, NY Times, Pivotal Tracker, Slicehost, tumblr, Twitter, WordPress, Yahoo, and Yelp are among the few. A plugin system allows anyone to add their own sites (and cookie styles) to the plugin.
Yikes! It goes without saying that this is a major security problem for anyone who uses unencrypted wireless networks. Includes on this list are many universities and companies such as Starbucks.
Secure Your Google Apps (Gmail, GDocs, GCal, etc)
If you are a Google user – meaning Gmail, Google Docs, Google…
Force HTTPS SSL Access for a URL with Apache
The situation is: you have an web application or URL that you…
Google Gmail, Docs, Apps and Reader Secured
For Firefox and Opera only: Use the Google Secure Pro Greasemonkey script…
Apache’s mod_proxy with Exchange’s Outlook Web Access
Apache’s mod_proxy module is simply one of the best Apache modules out…