The new Apache 2.4 has been released a few weeks ago and…
Browsing Tag
apache
12 posts
How to Stop an Apache DDoS Attack with mod_evasive
The first inkling that I had a problem with a DDoS (Distributed Denial of Service) attack was a note sent to my inbox:
lfd on server1.myhostname.com: High 5 minute load average alert – 89.14
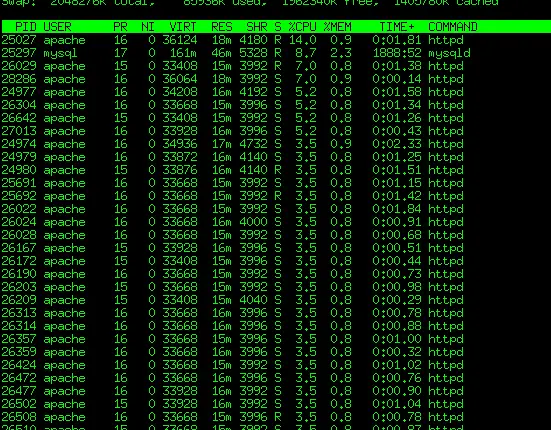
My initial thought was that a site on my server was getting Slashdotted or encountering the Digg or Reddit effect. I run Chartbeat on several sites where this occasionally happens and I will usually get an alert from them first. A quick look at the Extended status page from Apache showed that I had a much different kind of problem.
Password Protected Folder Gives 404 Not Found in WordPress Installation Sub-folder.
Came across this little maddening issue again today after fixing it a…
Simple Redirect Subdomain to a Directory
If you are running Apache for your web server, and mod_rewrite is…
Comprehensive .htaccess guide
The AskApache blog has a great comprehensive guide to .htaccess. A must…
Microsoft Office 2007 New Formats and your Apache server
If you upload those new fancy-shmancy file formats to your web server…
Use PHP, GD and .htaccess to Watermark All Images in a Directory
The goal here is to watermark all images in a certain directory,…