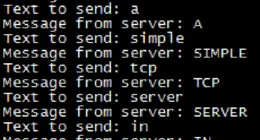
Recently came across a problem with one system authentication to another via…
Browsing Tag
ssh server
3 posts
Dead linux users?
Not dead as in dead, but dead as in the user has logged out of the system and for some reason their shell is still open. This might happen if your system crashes before you can log out, there are network problems and you are disconnected, or a number of other reasons. This article explains how to log these “dead” shell users out.
Block brute force password attempts via SSH
If you are a system administrator of a linux system, you may…