Readers should note that this applies to Ubuntu 8.10 Intrepid Ibex only!
ZFS is a relatively new filesystem created by Sun. It is released under the CDDL License which is incompatible with Linux’s GPL License, meaning that it can not be installed natively in the kernel. Therefore, for not it is relegated to addon packages and is brought to Ubuntu via the Fuse framework.
For more information on this see the Ubuntu Wiki article on ZFS.
The wiki article also explains this, but getting ZFS installed on Ubuntu is actually pretty straightforward by issuing these commands:
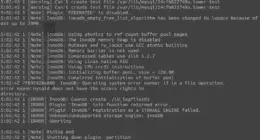
$ sudo echo "deb http://ppa.launchpad.net/brcha/ubuntu intrepid main" >> /etc/apt/sources.list.d/zfs-fuse.list $ sudo echo "deb-src http://ppa.launchpad.net/brcha/ubuntu intrepid main" >> /etc/apt/sources.list.d/zfs-fuse.list $ sudo apt-get update $ sudo apt-get install zfs-fuse
This installs zfs onto your system. Now to create your raid-z array! Its dead simple.
$ sudo zpool create media -m /storage raidz /dev/sda /dev/sdb /dev/sdc
In the above command:
- media is the name of the pool,
- /storage is the mount point (make sure it already exists),
- raidz is the type of mirroring/striping we are going to run (see more below), and
- the rest of the options are the devices you are adding into the pool.
Make sure the mount directory already exists.
The type of array you are creating can be the following:
- mirror will mirror the data across disks
- raidz will mirror and stripe data across all disks, allowing 1 drive to fail without losing data
- raidz2 will mirror and stripe data across all disks, allowing 2 drives to fail without losing data (but creating more overhead)
That really is it! You’ll then have a raid array, mounted to your indicated mount point. You can do all kinds of cool stuff with your pool, such as add disks, export the array to a file, import an exported file to the disk, create hot spares, and more.
After far as speed goes, I tested the pool performance with bonnie and also via real world estimates, and I’m only receiving about 20Mb/sec. Its not stellar and I plan to do some more testing as I haven’t tweaked my disks at all and I think I may be able to push it further. This slowness is caused by the checksumming that zfs does — it makes your data extremely safe but it does cause a lot of CPU overhead.
Hopefully ZFS will get more and more stable with time (although I haven’t had any problems with it so far!) and will be included in the Linux kernel, because it really is a great performing, easy to use file system. The uses for it could be tremendous, such as creating a desktop system as a zfs pool and creating instant disk backups from it with minimal overhead. Think: Time Machine for Linux!


18 comments
is there a way to use it with hardy?
is there a way to use it with hardy?
found it, hardy debs are also in the repository
found it, hardy debs are also in the repository
Is it possible to setup ZFS during the install?
Is it possible to setup ZFS during the install?
I do not believe so. Fuse-zfs is a addon and not supported in the main kernel, and therefore not available in the main install process.
I do not believe so. Fuse-zfs is a addon and not supported in the main kernel, and therefore not available in the main install process.
hey dude, zfs is not going to get included in the GPL linux kernel because of license incompatibilities.
hey dude, zfs is not going to get included in the GPL linux kernel because of license incompatibilities.
Fail fail fail
You cannot add disk to an already exsisting raidz or raidz2 array.
Learn about zfs first before you write crap like that.
Fail fail fail
You cannot add disk to an already exsisting raidz or raidz2 array.
Learn about zfs first before you write crap like that.
@Gumle
then what do you suppose ‘zpool add diskpool _’ does?
do shut up.
@Gumle
then what do you suppose ‘zpool add diskpool _’ does?
do shut up.
@colbs
Until block pointer rewrite is done, then Gumle is quite correct.
You can add disks to simple pool vdevs, you cannot currently add new columns (disks) to RAIDZ vdevs.
BP rewrite is not a priority at Sun, it should be noted.
@colbs
Until block pointer rewrite is done, then Gumle is quite correct.
You can add disks to simple pool vdevs, you cannot currently add new columns (disks) to RAIDZ vdevs.
BP rewrite is not a priority at Sun, it should be noted.
Debian has native kernel-level ZFS now:
http://tucobsd.blogspot.com/2010/08/apt-get-install-zfsutils.html
Debian has native kernel-level ZFS now:
http://tucobsd.blogspot.com/2010/08/apt-get-install-zfsutils.html
Comments are closed.